Recon-ng – An Open Source Intelligence (OSINT) Reconnaissance Framework
Recon-ng – An Open Source Intelligence (OSINT) Reconnaissance Framework
 |
Recon-ng is basically " A full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built-in convenience functions, interactive help, and command completion, Recon-ng provides a powerful environment in which open source web-based reconnaissance can be conducted quickly and thoroughly " which can perform open-source web-based information gathering for a given target. Recon-ng is loaded with a different type of in-built modules, such as reconnaissance, import, reporting, exploitation, and discovery modules. Usually, the type of information that can be gathered with these modules mainly includes contacts, credentials, social media profiles, and a handful of other information like IP, reverse IP, WHOIS information, and ports information which is very handy in any attack. Recon-ng can also look for certain vulnerabilities in a target web application, such as cross-site scripting, PunkSPIDER, and GHDB (Google Hacking Database).
Recon-ng was developed by Tim Tomes while at Black Hills Information Security.
Recon-ng Installation :
To install Recon-ng follow these simple steps :
Step #1
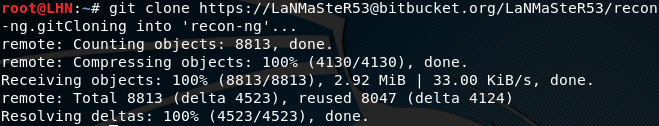
Clone the framework using the following command provided:
git clone https://LaNMaSteR53@bitbucket.org/LaNMaSteR53/recon-ng.git
Step #2
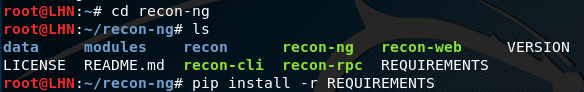
Move to the Recon-ng directory and run the REQUIRMENTS file.
cd recon-ng pip install -r REQUIREMENTS
How Recon-ng Works
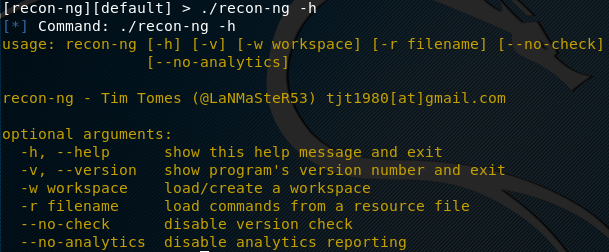
Recon-ng can be set into action using the following command.
./recon-ng
Step #1
To explore the modules, run the following command. The command displays all the modules along with the path required to run each module.
show modules
Step #2
In order to use any module, just type the following command.
use
Similarly, to set the target domain, use the following syntax.
set sourcerun
Examples :
example #1
If we want to run the XSSED vulnerabilities test module, we can do so in the following manner.
use recon/domains-vulnerabilities/xssed set source http://phptest.vulnweb.com run
The tool runs the defined module and displays the results on the screen as shown below.
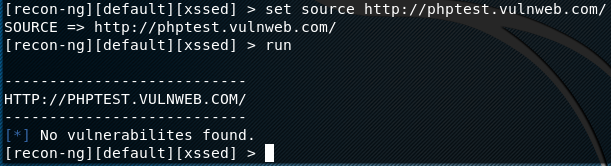
We can try other modules using the same approach. There are certain modules like Shodan, Facebook, Twitter, Instagram, etc that require API keys to fetch results. The API key for such modules can be added using the following command.
keys add
example #2
we have Shodan api key as SH1254AKD. We can add this API key as follows.
keys add shodan_api SH1254AKD
In order to see the configured keys in Recon-ng, use the following command.
keys list
This tool is really simple to use and it holds every result in its database for later use. The report generates is well-formatted and if in the future additional modules will be added to the framework.
want to know more!!! well you can check this out: Recon-ng


No comments
If you have any doubts, please let us Know.